Preface
A packet example from the Sharkfest Packet Challenge. Sharkfest is an annual conference organized by Wireshark, dedicated to sharing knowledge, experience, and best practices among Wireshark developers and user communities . I remember that it was held once a year in the early days, but in recent years it has become twice a year, one in the United States and one in other regions, such as Europe or Asia. Packet Challenge is one of the more interesting activities in the conference. Through a series of packet examples, participants can perform analysis challenges and test their comprehensive analysis capabilities.
Topic Information
This case is the first question Some HTTP in the Sharkfest 2019 EU Packet Challenge , and the packet trace file is SomeHTTP.pcapng .
The main description is as follows:
Something to get you warmed up.
1. What is the server IP address?
2. What is the hostname of the website requested by the browser?
3. What is the HTTP status code given by the web server?
4. What is the FQDN of the location the web server redirects to?
5. How many packets have a FIN flag set?
Just as “Something to get you warmed up” describes, this question is really quite simple.
Packet information
The basic information of the packet trace file is as follows:
λ capinfos SomeHTTP.pcapng
File name: SomeHTTP.pcapng
File type: Wireshark/... - pcapng
File encapsulation: Ethernet
File timestamp precision: microseconds (6)
Packet size limit: file hdr: (not set)
Number of packets: 8
File size: 1708 bytes
Data size: 1105 bytes
Capture duration: 2.409586 seconds
First packet time: 2014-03-04 01:19:57.323591
Last packet time: 2014-03-04 01:19:59.733177
Data byte rate: 458 bytes/s
Data bit rate: 3668 bits/s
Average packet size: 138.13 bytes
Average packet rate: 3 packets/s
SHA256: 59c3cb5bf2b529696e719088935b9911ba8b2666d4cb8c878317c0db8d6ba8b6
RIPEMD160: 5bba0f38317692a8ff1e5efe4430450366fe1c51
SHA1: 7315e55f08c58a06ba142f12c020055ecb5bd62b
Strict time order: True
Capture comment: https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=9848
Number of interfaces in file: 1
Interface #0 info:
Name = \Device\NPF_{1859BC84-0689-4EE4-9F7F-85D093A8F58B}
Encapsulation = Ethernet (1 - ether)
Capture length = 65535
Time precision = microseconds (6)
Time ticks per second = 1000000
Time resolution = 0x06
Operating system = 32-bit Windows 7 Service Pack 1, build 7601
Number of stat entries = 1
Number of packets = 8Captured directly via Wireshark on a Windows 7 system, without truncation, 8 packets were captured, the capture duration was 2.4 seconds, and the average rate was 3668 bps.
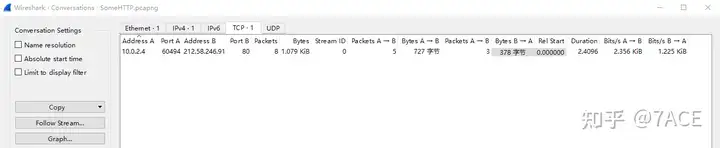
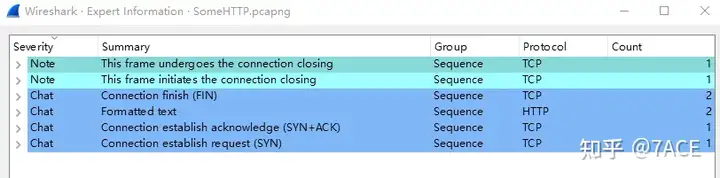
The session information and expert information are shown as follows: there is only one TCP stream 0, HTTP port 80 on the server, no alarm level information, and it is basically normal.
Packet Analysis
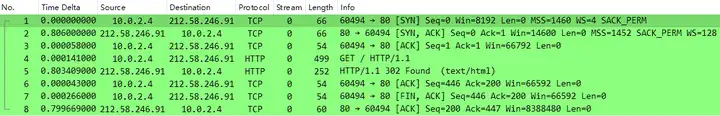
Expand the data packet file information as follows:
1. What is the server IP address?
What is the server IP address?
Analysis steps
There are no steps, and the answer is obvious.
Analyze the answer
The server IP address is: 212.58.246.91.
2. What is the hostname of the website requested by the browser ?
What is the hostname of the website that the browser is requesting?
Analysis steps
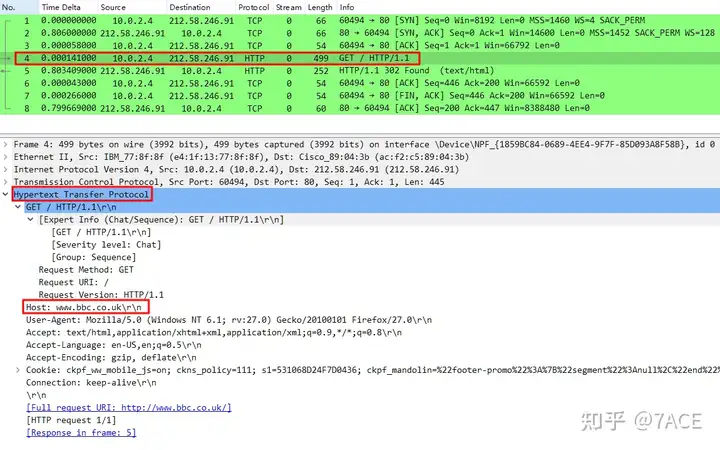
Client No.4 HTTP GET request, the details of the expanded data packet are as follows
λ tshark -r SomeHTTP.pcapng -Y "http.host"
4 0.806199 10.0.2.4 → 212.58.246.91 HTTP 499 GET / HTTP/1.1
λ tshark -r SomeHTTP.pcapng -Y "http.host" -T fields -e http.host
www.bbc.co.ukAnalyze the answer
The hostname of the website requested by the browser is: http://www.bbc.co.uk.
3. What is the HTTP status code given by the web server?
What is the HTTP status code given by the web server?
Analysis steps
Server No.5 HTTP Response response, expand the data packet details as follows
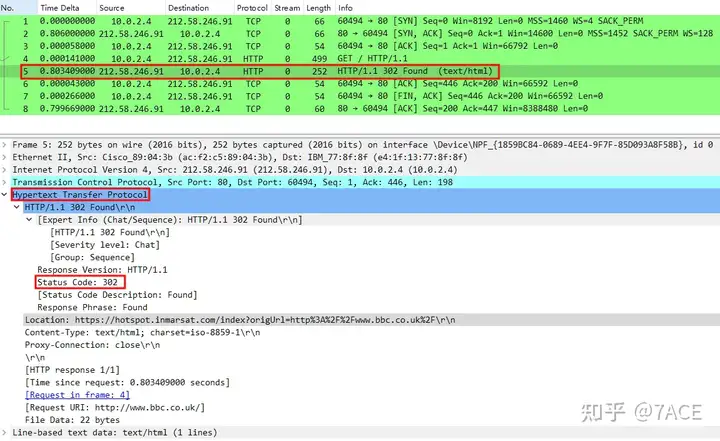
λ tshark -r SomeHTTP.pcapng -Y "http.response.code"
5 1.609608 212.58.246.91 → 10.0.2.4 HTTP 252 HTTP/1.1 302 Found (text/html)
λ tshark -r SomeHTTP.pcapng -Y "http.response.code" -T fields -e http.response.code
302Analyze the answer
The HTTP status code given by the web server is: 302.
4. What is the FQDN of the location the web server redirects to?
What is the FQDN of the location that the web server redirects to?
Analysis steps
The server-side No.5 HTTP Response response is still the same. The details of the data packet are as follows
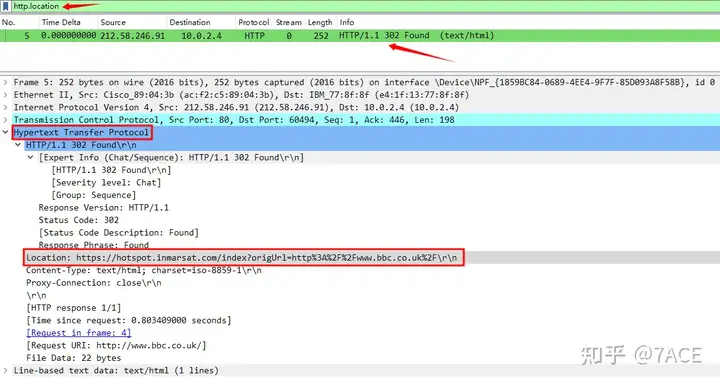
λ tshark -r SomeHTTP.pcapng -Y "http.location"
5 1.609608 212.58.246.91 → 10.0.2.4 HTTP 252 HTTP/1.1 302 Found (text/html)
λ tshark -r SomeHTTP.pcapng -Y "http.location" -T fields -e http.location
https://hotspot.inmarsat.com/index?origUrl=http%3A%2F%2Fwww.bbc.co.uk%2F
λ tshark -r SomeHTTP.pcapng -Y "http.location" -T fields -e http.location | awk -F "/" '{print $3}'
hotspot.inmarsat.comAnalyze the answer
The FQDN of the location to which the web server redirects is: http:// hotspot.inmarsat.com.
5. How many packets have a FIN flag set?
How many packets have the FIN flag set ?
Analysis steps
By displaying the filter expression, tcp.flags.fin==1 we can see
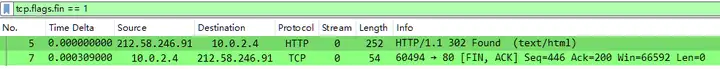
λ tshark -r SomeHTTP.pcapng -Y "tcp.flags.fin==1" | wc -l
2Analyze the answer
How many packets have the FIN flag set: 2.



