Since its inception in 1997 by Gerald Combs to address network issues at a small ISP, Wireshark (originally known as Ethereal) has evolved into one of the most popular tools for packet-level analysis of network and application protocols. Its open-source nature, extensive feature set, coverage of over 1000 protocols, and contributions from a global community of over 800 developers have contributed to its widespread adoption.
This introductory chapter will guide you through installing Wireshark on your system and performing useful tasks, setting the stage for deeper exploration of its capabilities and supporting concepts.
In this chapter, we will explore the following topics:
- Installing Wireshark
- Performing a packet capture
- Wireshark user interface essentials
- Using display filters to isolate traffic of interest
- Saving a filtered packet trace file
The chapters that follow will build on and provide the supporting concepts for these basic functions to allow you to develop the Wireshark skills that are most applicable to your technical role and objectives.
Installing Wireshark
Wireshark is compatible with 32- and 64-bit Windows (XP, Win7, Win8.1, etc.), Mac OS X (10.5 and higher), and most Linux/Unix distributions. Installation on Windows and Mac systems is straightforward with installers available from the Wireshark website. It’s also a standard package in many Linux distributions, with third-party installers listed on the Wireshark download page for various *nix platforms. If needed, you can compile Wireshark from the source code for your environment. During installation, Wireshark installs the WinPcap (Windows) or libpcap (Linux/Unix/Mac) libraries for packet capture and filtering functions.
Note: You might need administrator (Windows) or root (Linux/Unix/Mac) privileges to install Wireshark and the WinPcap/libpcap utilities on your workstation.
To install Wireshark on a Windows or Mac system, visit the Wireshark website (https://www.wireshark.org/) and click the Download button. The website will auto-detect your operating system, and the appropriate installer will be highlighted for download. Simply click the highlighted link to download the installer.
Note: If you already have Wireshark installed, an autoupdate feature will notify you of available version updates when you launch Wireshark.
Installing Wireshark on Windows
In the following screenshot, the Wireshark download page has identified that a 64-bit Windows installer is appropriate for this Windows workstation:
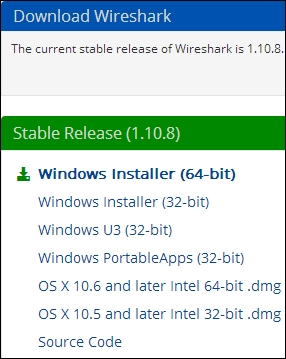
Clicking on the highlighted link downloads a Wireshark-win64-1.10.8.exe file or similar executable file that you can save on your hard drive. Double-clicking on the executable starts the installation process. You need to follow these steps:
- Agree to the License Agreement.
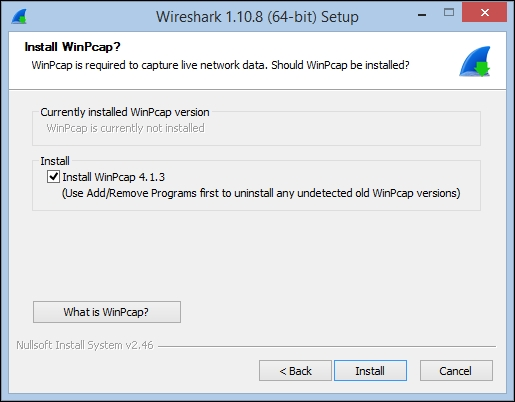
- Accept all of the defaults by clicking on Next for each prompt, including the prompt to install WinPcap, which is a library needed to capture packets from the Network Interface Card (NIC) on your workstation.
- Early in the Wireshark installation, the process will pause and prompt you to click on Install and several Next buttons in separate windows to install WinPcap.
- After the WinPcap installation is complete, click through the remaining Next prompts to finish the Wireshark installation
Installing Wireshark on Mac OS X
Installing Wireshark on a Mac follows a similar process to the Windows installation, but instead of WinPcap, it installs libpcap, the packet capture library for Mac and Unix systems, without any prompting.
However, there are two additional requirements that may need to be addressed during a Mac installation:+
- The first is to install X11, a windowing system library. If this is needed for your system, you will be informed and provided a link that ultimately takes you to the XQuartz project download page so you can install this package.
- The second requirement that might come up is if upon starting Wireshark, you are informed that there are no interfaces on which a capture can be done. This is a permissions issue on the Berkeley packet filter (BPF) that can be resolved by opening a terminal window and typing the following command:bash-3.2$ sudo chmod 644 /dev/bpf*
For a more permanent permissions solution on your system, you can search online.
Installing Wireshark on Linux/Unix platforms can vary based on your specific environment. Typically, Wireshark is available through the package management systems of most Linux distributions. Check Chapter 2, Networking for Packet Analysts, or the Wireshark user documentation at www.wireshark.org/docs/wsug_html_chunked/ChapterBuildInstall.html for guidance.
Performing your first packet capture
When you first start Wireshark, you are presented with an initial Start Page as shown in the following screenshot:
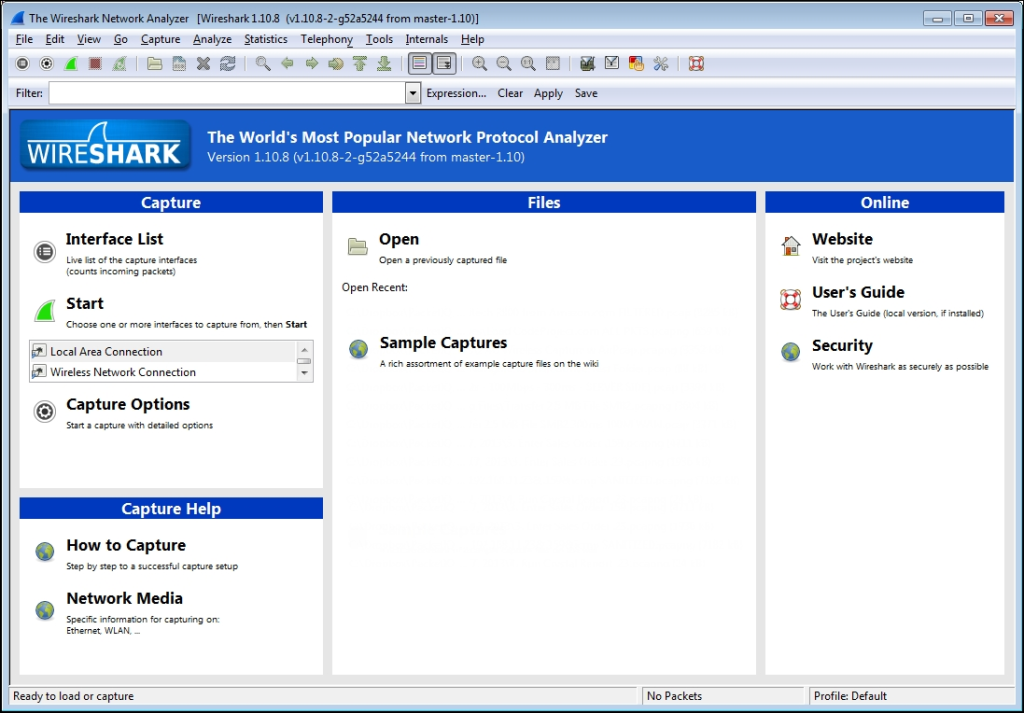
Don’t get too fond of this screen. Although you’ll see this every time you start Wireshark, once you do a capture, open a trace file, or perform any other function within Wireshark, this screen will be replaced with the standard Wireshark user interface and you won’t see it again until the next time you start Wireshark. So, we won’t spend much time here.
Selecting a network interface
If you’re unsure which network interface to select for packet capture, Wireshark provides an easy solution. Simply click on “Interface List” on the Wireshark start page, or go to “Interfaces” from the Capture menu, or click on the first icon on the icon bar.
The Wireshark Capture Interfaces window displays a list and description of all network interfaces on your machine, along with their assigned IP addresses (if any), and packet counters. You can click on an IPv6 address to toggle and display the IPv4 address, as shown in the screenshot below:
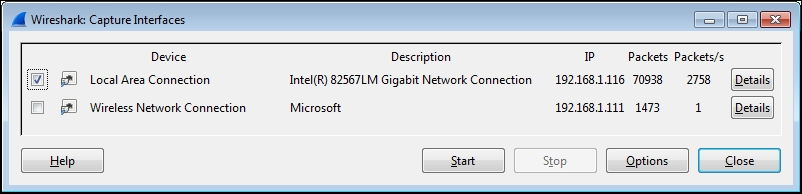
Note: On Linux/Unix/Mac platforms, you might also see a loopback interface that can be selected to capture packets being sent between applications on the same machine. However, in most cases, you’ll only be interested in capturing packets from a network interface.
The objective is to determine the active network interface used for Internet communication when accessing a website. If you have both wired and wireless connections enabled, the active interface is likely the one with steadily increasing packet counts and an active packets/s rate. Another indicator is if an interface has an assigned IP address while others do not. If unsure, open a browser and navigate to a website, observing the packet and packets/s counters to identify the interface with the most activity.
Performing a packet capture
Once you’ve found the correct interface, simply check the box next to it and click the Start button at the bottom of the Capture Interfaces window. Wireshark will begin capturing all the packets visible from that interface, including those sent to and from your workstation. You’ll notice a wide range of packets scrolling by in the top section, known as the Packet List pane; if you don’t see this, try another interface.
It’s surprising to see the amount of background traffic on a typical network, including broadcast packets from devices advertising their names, addresses, and services, as well as traffic generated by your own workstation for running applications and services. Your Packet List pane in Wireshark may resemble the following screenshot, but for now, we can disregard it:
We’re ready to generate some traffic that we’ll be interested in analyzing. Open a new Internet browser window, enter www.wireshark.org in the address box, and press Enter.
When the https://www.wireshark.org/ home page finishes loading, stop the Wireshark capture by either selecting Stop from the Capture menu or by clicking on the red square stop icon that’s between the View and Go menu headers.
Wireshark user interface essentials
After completing your initial capture, you’ll be greeted with the standard Wireshark user interface. Before diving deeper, let’s briefly introduce the primary components of this interface so you can easily follow along as we analyze the data.
The default Wireshark user interface consists of eight main sections or elements, depicted in the following screenshot:
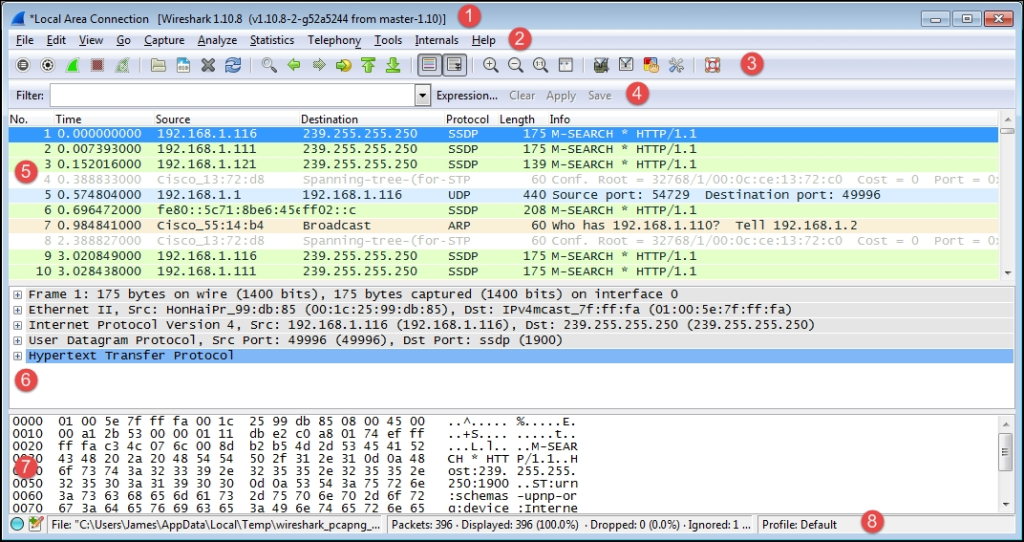
Let’s look at the eight significant sections in detail:
- Title: This area reflects the interface from where a capture is being taken or the filename of an open packet trace file
- Menu: This is the standard row of main functions and subfunctions in Wireshark
- Main toolbar (icons): These provide a quick way to access the most useful Wireshark functions and are well worth getting familiar with and using
- Display filter toolbar: This allows you to quickly create, edit, clear, apply, and save filters to isolate packets of interest for analysis
- Packet list pane: This section contains a summary info line for each captured packet, as well as a packet number and relative timestamp
- Packet details pane: This section provides a hierarchical display of information about a single packet that has been selected in the packet list pane, which is divided into sections for the various protocols contained in a packet
- Packet bytes pane: This section displays the selected packets’ contents in hex bytes or bits form, as well as an ASCII display of the data that can be helpful
- Status bar: This section provides an expert info indicator, edit capture comments icon, trace file path name and size information, data on the number of packets captured and displayed and other info, and a profile display and selection section
Filtering out the noise
In your packet capture, you’ll find packets related to loading the Wireshark home page. But how do you isolate and view only those packets amid all the background noise?
The most straightforward method is to filter out all packets except those between the IP address of the Wireshark website and your workstation’s IP address using a display filter. Alternatively, you can investigate all conversations by IP address or hostname, sorted by activity, to identify your target IP address or hostname.
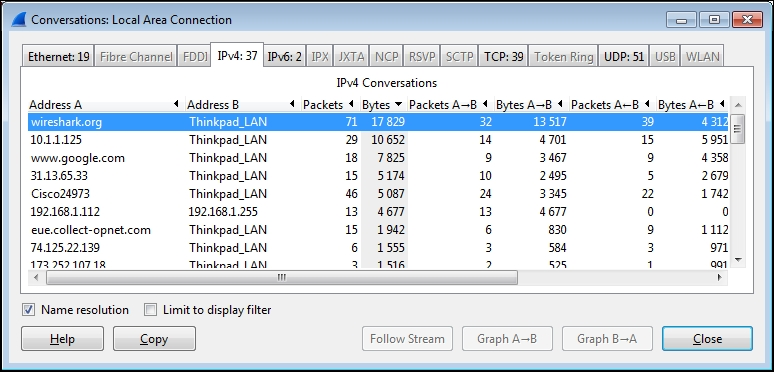
To do this in Wireshark, go to the Statistics menu and select Conversations. In the Conversations window, choose the IPv4 tab. Here, you’ll see a list of network conversations, including the total number of packets and bytes exchanged between each pair of addresses, along with their start times, durations, and average data rates.
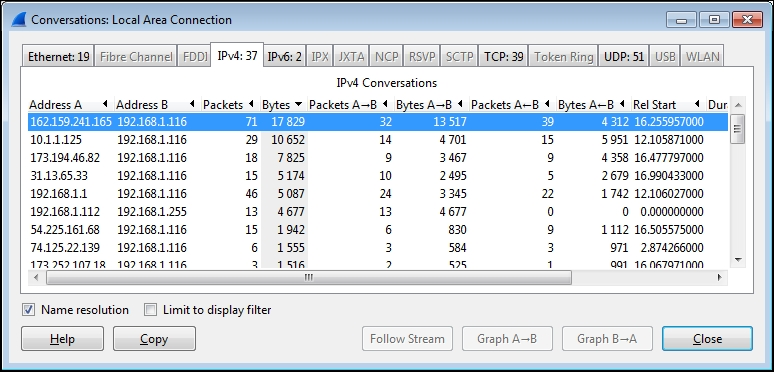
To prioritize the busiest conversations, known as the Top Talkers, in the list, click on the Bytes column header twice. This will organize the conversations by volume, with the most significant traffic at the top. If there isn’t much background traffic, the traffic from https://www.wireshark.org/ should dominate the list.
In the example, the conversation between IP addresses 162.159.241.165 and 192.168.1.116 has the highest overall volume. Checking the Bytes A->B column, most of the traffic flows from 162.159.241.165 to 192.168.1.116. However, how do we confirm if this is the conversation we’re interested in?
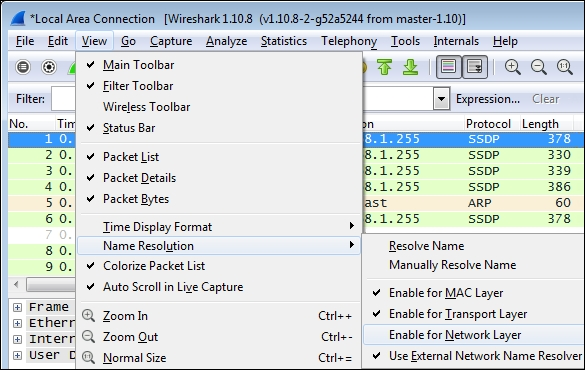
We need to resolve the IP addresses to hostnames or website addresses. Wireshark can do this by enabling Network Name Resolution, which attempts to resolve IP addresses using reverse DNS queries. Note that this option may not be enabled by default.
To enable Name Resolution, go to View | Name Resolution | Enable for Network Layer, and ensure Use External Network Name Resolver is enabled. Wireshark will then attempt to resolve all IP addresses to hostnames or website addresses, displaying them in the packet list and Conversations window.
Ensure that the Name Resolution option at the bottom of the Conversations window is also enabled to see the resolved names or IP addresses.
At this point, you should see the conversation pair between wireshark.org and your workstation at or near the top of the list, as shown in the following screenshot. Of course, your workstation will have a different name or may only appear as an IP address, but identifying the conversation to wireshark.org has been achieved.
Applying a display filter
You now want to see just the conversation between your workstation and wireshark.org, and get rid of all the extraneous conversations so you can focus on the traffic of interest. This is accomplished by creating a filter that only displays the desired traffic.
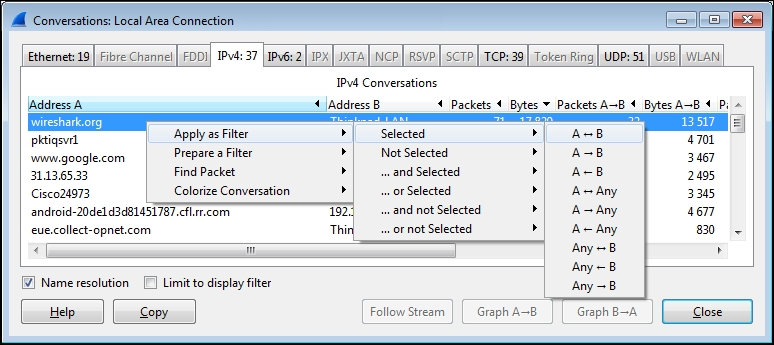
Right-click on the line containing the wireshark.org entry and navigate to Apply as Filter | Selected | A<->B, as shown in the following screenshot:
Wireshark will create and apply a display filter string that isolates the displayed traffic to just the conversation between the IP addresses of wireshark.org and your workstation, as shown in the following screenshot. Note that if you create or edit a display filter entry manually, you will need to click on Apply to apply the filter to the trace file (or Clear to clear it).
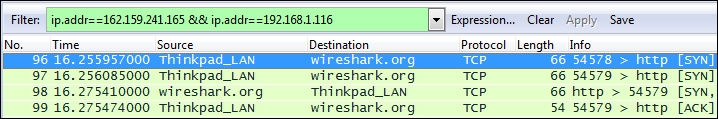
This specific display filter syntax operates with IP addresses, rather than hostnames, using the ip.addr== (IP address equals) syntax for each node along with the && (and) logic operator to construct a string that filters packets containing both specified IP addresses. This filter type is commonly used for packet analysis.
As you scroll through the Packet List pane, you’ll notice that all packets, except those between your workstation and wireshark.org, have disappeared. They’re not truly gone; they’re just hidden. You can observe gaps in the numbering sequence in the Packet No. column, indicating hidden packets.
Saving the packet trace
Now that you’ve isolated the relevant traffic using a display filter, you can save a new packet trace file containing only the filtered packets.
This serves two purposes. Firstly, you can close Wireshark, return later, open the filtered trace file, and resume your analysis where you left off, as well as have a record of the capture for future reference, such as in troubleshooting scenarios.
Secondly, working with a smaller, more focused trace file containing only the packets you want to analyze makes it much easier and quicker to navigate through Wireshark’s various screens and functions.
To create a new packet trace file containing the filtered/displayed packets, select Export Specified Packets from the Wireshark File menu.
Navigate to or create a folder to store your Wireshark trace files, and enter a filename for the trace file you want to save. In this example, the filename is wireshark_website.pcapng. By default, Wireshark saves the trace file in the pcapng format, which is the preferred format. If you don’t specify a file extension with the filename, Wireshark will provide the appropriate extension based on the Save as type selection.
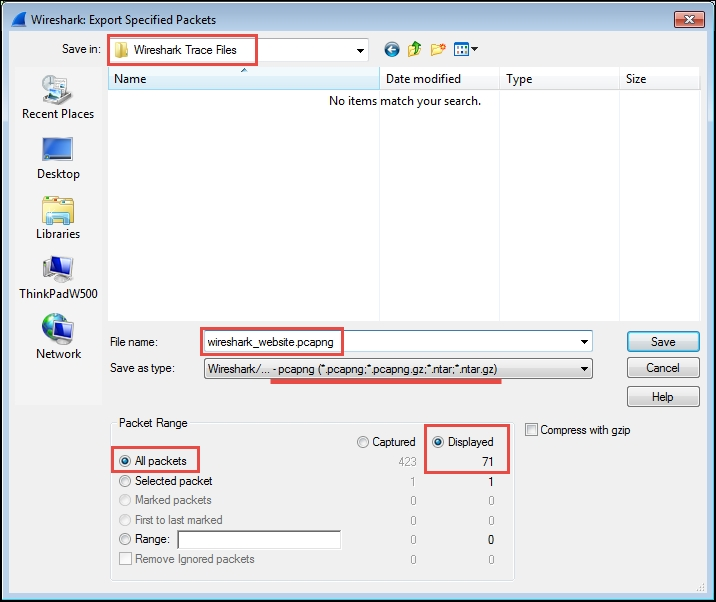
By default, Wireshark selects the “All packets” option, but when a display filter is applied (as in this case), it automatically switches to the “Displayed” option, which only saves the filtered packets. If you want to save all packets regardless of the filter, you need to manually select the “Captured” option.
Once you’ve entered a filename and confirmed all the save selections, simply click on “Save” to save the new packet trace file.
After saving the trace file, it’s important to note that Wireshark still retains all the original packets from the capture in memory. You can view them again by clicking on “Clear” in the Display Filter Toolbar menu. If you want to continue working with the newly saved trace file, you’ll need to open it by clicking on “Open” in the File menu (or “Open Recent” if it appears in the File menu).
Selecting a network interface
When you’re unsure which network interface to select for packet capture, Wireshark provides an easy solution. Simply click on “Interface List” on the Wireshark start page, or access it through the Capture menu or the icon bar.
The Wireshark Capture Interfaces window displays a list of all network interfaces on your machine along with their descriptions and assigned IP addresses (if available). Additionally, it shows counters such as the total number of packets seen on each interface since the window opened, and a packets per second (packets/s) counter. If an interface has an IPv6 address assigned, you can toggle it to display the IPv4 address by clicking on it. See the screenshot below for reference:
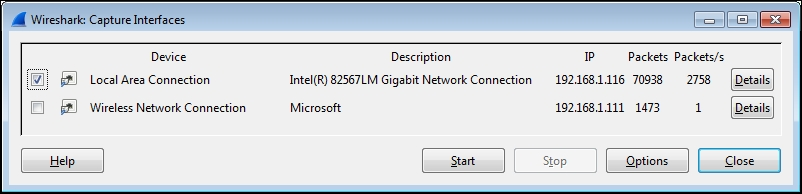
Note: On Linux/Unix/Mac platforms, you might also see a loopback interface that can be selected to capture packets being sent between applications on the same machine. However, in most cases, you’ll only be interested in capturing packets from a network interface.
The objective is to determine the active interface that connects to the Internet when you browse a website. Typically, a wired LAN connection is the active interface, but you may also have an enabled wireless interface. The most reliable indicator is the interface with a higher number of steadily increasing packets and packets/s. You can also check if an interface has an assigned IP address. If uncertain, open a browser window, visit a website, and observe the packets and packets/s counters to identify the interface with the most activity.
Performing a packet capture
After selecting the correct interface, check the checkbox next to it and click the Start button at the bottom of the Capture Interfaces window. Wireshark will begin capturing all packets visible from that interface, including those sent to and from your workstation. The Packet List pane will display a wide variety of packets scrolling by, which is normal. If you don’t see this, try a different interface.
It’s surprising how much background traffic exists on a typical network, including broadcast packets from devices advertising their names, addresses, and services, as well as requests for addresses from other devices. Additionally, your own workstation generates a fair amount of traffic from background applications and services, contributing to the noise. While the Packet List pane may seem overwhelming, we can ignore this background traffic for now.
We’re ready to generate some traffic that we’ll be interested in analyzing. Open a new Internet browser window, enter www.wireshark.org in the address box, and press Enter.
When the https://www.wireshark.org/ home page finishes loading, stop the Wireshark capture by either selecting Stop from the Capture menu or by clicking on the red square stop icon that’s between the View and Go menu headers.
Wireshark user interface essentials
After finishing your first capture, you’ll land on the main screen of the Wireshark user interface. Before delving deeper, let’s quickly introduce the key sections of this interface for better understanding as we proceed with the analysis process.
The default Wireshark user interface comprises eight significant sections or elements, depicted in the following screenshot:
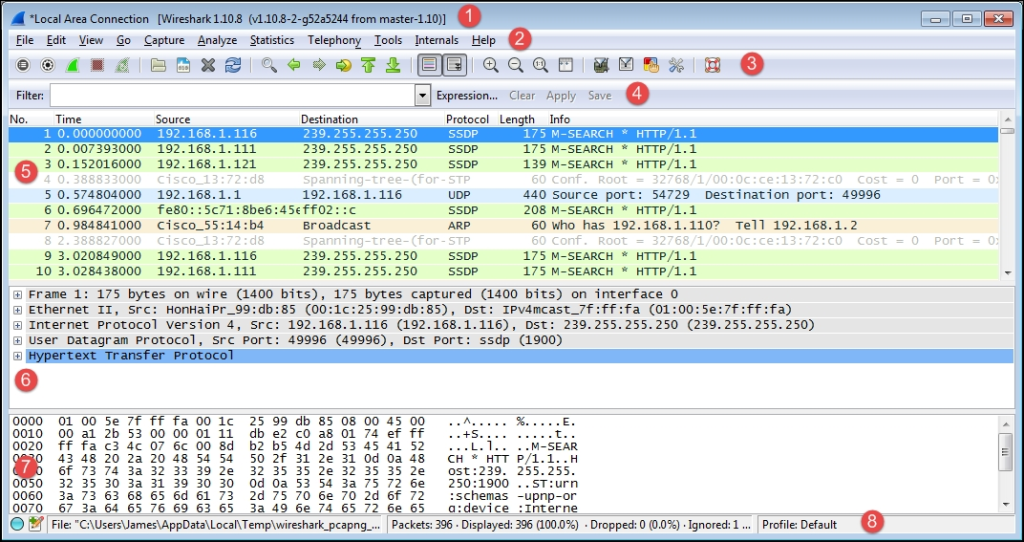
Let’s look at the eight significant sections in detail:
- Title: This area reflects the interface from where a capture is being taken or the filename of an open packet trace file
- Menu: This is the standard row of main functions and subfunctions in Wireshark
- Main toolbar (icons): These provide a quick way to access the most useful Wireshark functions and are well worth getting familiar with and using
- Display filter toolbar: This allows you to quickly create, edit, clear, apply, and save filters to isolate packets of interest for analysis
- Packet list pane: This section contains a summary info line for each captured packet, as well as a packet number and relative timestamp
- Packet details pane: This section provides a hierarchical display of information about a single packet that has been selected in the packet list pane, which is divided into sections for the various protocols contained in a packet
- Packet bytes pane: This section displays the selected packets’ contents in hex bytes or bits form, as well as an ASCII display of the data that can be helpful
- Status bar: This section provides an expert info indicator, edit capture comments icon, trace file path name and size information, data on the number of packets captured and displayed and other info, and a profile display and selection section


