POP3 password brute force attacks are a type of network attack where attackers use automated tools to try numerous username and password combinations to gain unauthorized access to a POP3 (Post Office Protocol version 3) email server. POP3 is a protocol used for retrieving emails from a server, so a successful attack could lead to unauthorized email access, data theft, or account misuse. Therefore, you can keep reading to get the best brute force protection for POP3.
Characteristics of POP3 Password Brute Force Attacks
- Automated Attempts: Attackers use tools to systematically try many password combinations.
- Repeated Attempts: Attackers attempt different username and password combinations until they find a valid one.
- Exploitation of Weak Passwords: Attackers often target accounts with weak or commonly used passwords.
Best Brute Force Protection for POP3 – Sax2 IDS
Step 1. Install Sax2
After installing Sax2 NIDS correctly, you will see the following icon on the desktop, double-click it to start Sax2 NIDS
Step 2. Start Detecting
After starting Sax2, click the “Start” button on the main interface to start the intrusion detection, please see the figure below:
Step 3. View Intrusion Events
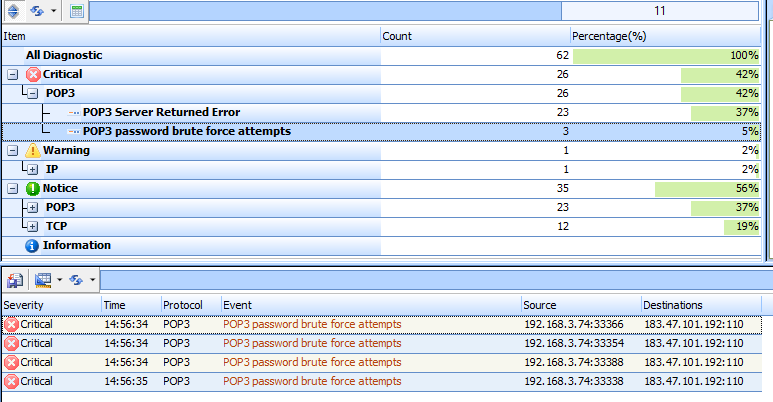
The “Events” viewing window is one of the most important features of Sax2 NIDS and the main place to analyze intrusion events. In order to view the event, first switch to the Events window. Take a look at the following figure, from which you can see that Sax2 has successfully detected the POP3 password brute force attacks.
Defending Against POP3 Password Brute Force Attacks
- Use Strong Passwords:
- Ensure POP3 accounts have complex and unique passwords, avoiding simple or easily guessable ones.
- Limit Login Attempts:
- Configure the POP3 server to limit the number of login attempts, such as locking accounts after a certain number of failed attempts or using CAPTCHA.
- Enable Multi-Factor Authentication (MFA):
- Implement MFA for POP3 accounts to add an extra layer of security beyond just passwords.
- IP and Geographic Restrictions:
- Restrict access to the POP3 server by IP address range, and consider whitelisting known IPs or using geographic restrictions.
- Use Secure Connections:
- Use secure POP3 connections (such as POP3 over SSL/TLS) to encrypt data in transit, protecting it from interception.
- Regular Updates and Patching:
- Keep POP3 server software and related systems updated to patch known vulnerabilities and improve security.
- Log Auditing and Analysis:
- Regularly review and analyze logs for signs of brute force attacks and take necessary actions based on findings.
- Deploy Intrusion Detection Systems (IDS):
- Utilize IDS to monitor and respond to suspicious login activities and potential attacks.
Conclusion
By implementing these detection and defense strategies, you can effectively reduce the risk of POP3 password brute force attacks and enhance the security of your email server.


