Preface
With the growing use of network packet analysis technology, security concerns related to packet capture and analysis have become increasingly prominent. Since network packets often contain sensitive information, the need to address privacy risks during information sharing is crucial. Using Packet Anonymization Tools is a key approach to mitigate these risks and ensure data security while handling network traffic.
In our work, we sometimes encounter similar scenarios as follows, including:
- When a production business system encounters a problem, the network data packets collected need to be provided to internal or external engineers for troubleshooting and analysis ;
- When discussing technical issues with friends or consulting or discussing on external public platforms, some network data packet information that needs to be shared, including screenshots or tracking files ;
- When publishing technical articles and materials externally, they may involve quoting network data packet information.
……
So how do we ensure the security of these shared data package information? One way is to anonymize the data package information. This article will briefly explain it from the perspective of a user of anonymization tools.
If there is any misunderstanding in the non-security direction, please feel free to ask for advice.
Anonymization
What is anonymization? Anonymization is an effective technology to solve the dilemma of “data availability” and ” privacy protection “, which can achieve “processing that cannot identify specific individuals and cannot be restored”. Literally, it is anonymous processing, and “anonymity” can be understood as making the “natural person” represented by the original data record “identity anonymous”. Specifically, through various technical means, such as deleting identifiers , generalization, and noise addition, the association between natural persons and data records is cut off, thereby not only retaining the required data value, but also reducing the risk of privacy leakage.
As for the anonymized data packet trace file information, it may include two aspects of processing: data packet information screenshots or the data packet trace file itself.
- Data packet information screenshot
- Mosaic is the first choice, and the relevant information under image processing, such as the IP address part ~ P-picture tool;
Edit Resolved NameOr you can directly use Wireshark ‘s method to name them Client and Server.
2. Packet capture files
- Through the slicing tool, only the required header part is left for analysis; (the disadvantage is that it cannot go deep into the application layer)
- Packet anonymization tools (also known as packet modifiers), in-depth processing, manual or batch processing of information such as MAC addresses, IP addresses, TCP/UDP ports and application layer. ( The focus of this article )
tool
There are actually many anonymization tools. You can find the one that suits you according to the actual scenario. They are as follows:
- TraceWrangler
- editcap
- tcprewrite
- Colai Data Packet Generator
- Bit-Twist
- Hex Editor
TraceWrangler
TraceWrangler is a tool developed by Jasper Bongertz, a core technician of Wireshark. Those who often watch Sharkfest should be familiar with this tool. He gives a special speech on TraceWrangler at almost every annual conference. To be honest, personally, since I have used TraceWrangler, I rarely use other tools. TraceWrangler can only be described as a magical tool, at least it can fully cover the scenarios I want to use to share data packet file information, which is why I put it in the first introduction.
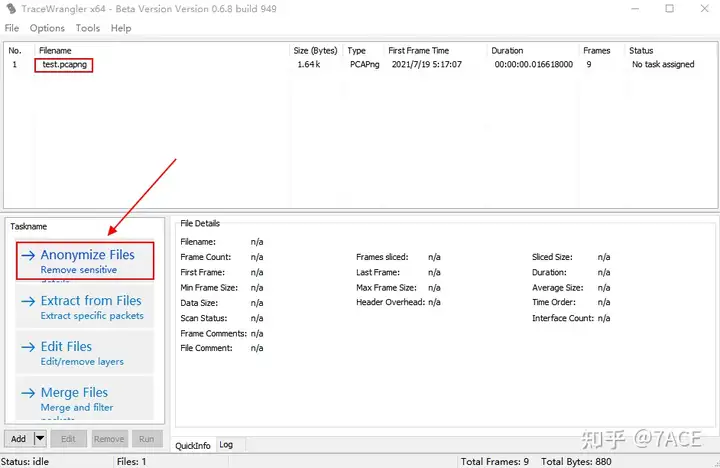
Adding and anonymizing files
The default task includes some common anonymization options, including:
- Payload , which can remove unknown application layers, truncate a layer, truncate by offset, and replace a specified string;
- PCAPng , for pcapng format files, can anonymize comments, interface names, name resolution , etc.;
- Layer2 , you can specify or randomly replace the MAC address and VLAN ID, replace CRC, etc.
- Layer3 , can specify or randomly replace IP addresses and IP IDs, ICMP control information , etc.;
- Layer4 , you can specify or replace TCP, UDP port information, etc.
- Others , including special application layer information, etc.
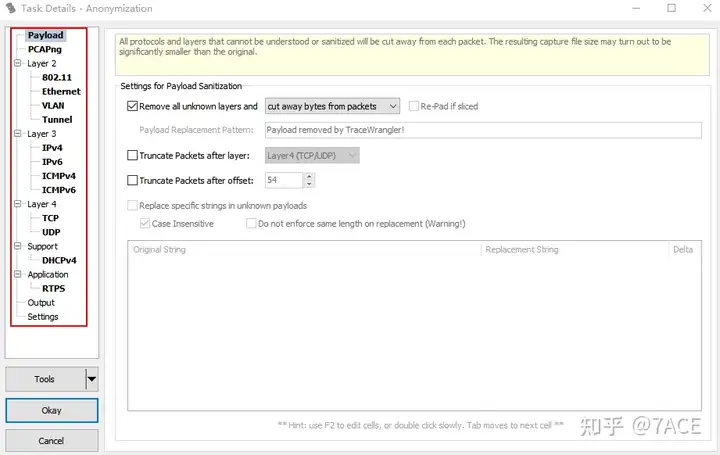
ToolsOf course, you can also clear all default options through Options , and only process a certain field anonymously according to your needs, or set a profile that you often use.
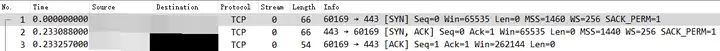
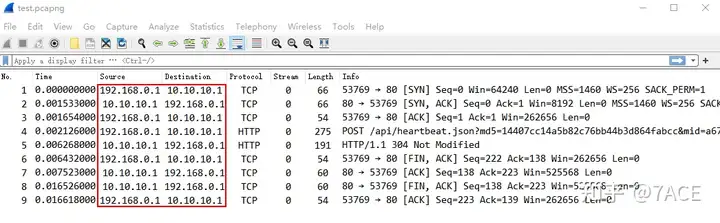
The following is a simple task of anonymizing an IPv4 address. The original file information is as follows:
Only IPv4 address information is processed. The source IP 192.168.0.1 is replaced with 100.1.1.1 and the destination IP 10.10.10.1 is replaced with 200.1.1.1. Of course, IPv4 addresses can also be processed randomly and anonymously. See Process remaining IP addressesthe following options.
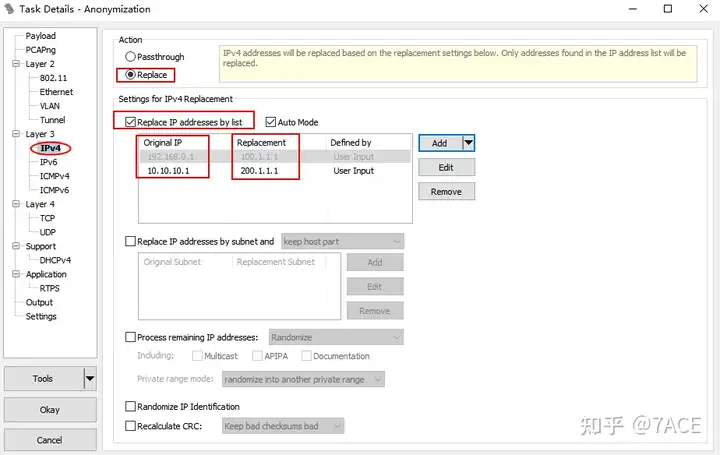
Click Okayto return to the main interface and generate an anonymized file task (including file details on the right). Then click Run, and an anonymized file will be automatically generated next to the original file. If the original file name is test.pcapng, the anonymized file will be test_anon.pcapng.

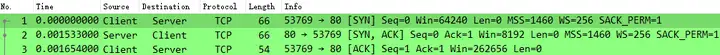
The test_anon file information is processed as follows
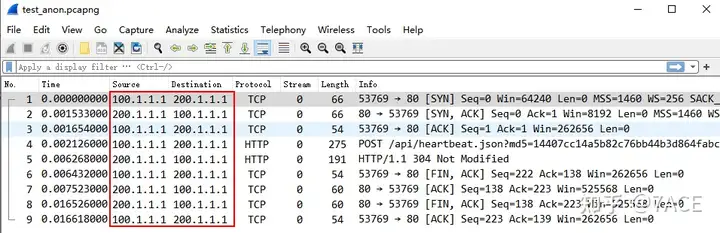
Isn’t it very simple?
Colai Data Packet Generator
The Kelai Packet Generator is one of the tools included with the installation of the Kelai Network Analysis System Technical Exchange Edition. After importing the packet file, a list of all packets will appear in the right column. Click a packet and the decoding information will automatically appear in the left column. You can directly perform detailed decoding editing in the upper left column, or perform hexadecimal editing in the lower left column. Other functions include adding or inserting packets of some common protocols, including ARP packets, IPv4 packets, TCP packets, etc. Of course, the modified packets can also be sent out through network card simulation. Also compared to specialized anonymization tools, functions such as batch editing are not yet perfect.
Editcap
Editcap is one of the optional tools that comes with the Wireshark program when it is installed. It is a command line tool for editing data packet files. Strictly speaking, it is not a professional anonymization tool. The related functions it uses include packet length truncation, packet time modification, random change of data fields, offset bit field modification, etc. Because it is a command line tool, for anonymization operations, you need to be very familiar with the relevant network protocol data packets. Moreover, it is not very convenient for non-professional tools and some graphical tools.
Tcprewrite
The tool tcprewrite under tcpreply – pcap file editor which rewrites TCP/IP and Layer 2 packet headers can modify the header information of each layer [https://github.com/appneta/tcpreplay](https://github.com/appneta/tcpreplay). For details, see
Tcpreplay is a suite of GPLv3 licensed utilities for UNIX (and Win32 under Cygwin) operating systems for editing and replaying network traffic which was previously captured by tools like tcpdump and Wireshark. It allows you to classify traffic as client or server, rewrite Layer 2, 3 and 4 packets and finally replay the traffic back onto the network and through other devices such as switches, routers, firewalls, NIDS and IPS’s. Tcpreplay supports both single and dual NIC modes for testing both sniffing and in-line devices.
WireEdit
WireEdit is a visual editing tool for editing network data packets . It comes from the same company as Omnipeek. For more information, see https://omnipacket.com/As a commercial product, WireEdit does not require a commercial license when used as a packet analyzer, but does require a commercial license when used as a packet editor .
WireEdit allows WYSIWYG editing of Pcap data in situ for any network stack at any stack layer while preserving the binary integrity of the data. Data editing is done in a break-proof manner with the lengths, checksums, offsets, and other inter and intra-packet dependencies recalculated on-the-fly for all affected packets and protocol layers.
Hex Editor
There are many hex editors to choose from, including the common notepad++ (load the HEX-Editor plug-in), WinHex and 010Editor, etc. For example, 010Editor has added the parsing of Network pcap and pcapng files through templates to facilitate editing. These tools, like editcap, require a good understanding of the relevant network protocol data packets, so it is not very easy to use.



